“I was told to buy a software or lose my computer. I ignored it”: a study of ransomware Simoiu et al., SOUPS 2019
This is a very easy to digest paper shedding light on the prevalence of ransomware and the characteristics of those most likely to be vulnerable to it. The data comes from a survey of 1,180 US adults conducted by YouGov, an online global market research firm. YouGov works hard to ensure respondent participation representative of (in this case) the general population in the U.S., but the normal caveats apply.
We define ransomware as the class of malware that attempts to defraud users by restricting access to the user’s computer or data, typically by locking the computer or encrypting data. There are thousands of different ransomware strains in existence today, varying in design and sophistication.
The survey takes just under 10 minutes to complete, and goes to some lengths to ensure that self-reporting victims really were victims of ransomware (and not some other computer problem).

For respondents that indicated they had suffered from a ransomware attack, data was collected on month and year, the name of the ransomware variant, the ransom demanded, the payment method, whether or not they paid the ransom, whether access was restored if they did, and what strategies they used to try and remove the ransomware. Responses were independently reviewed to ensure the descriptions given were consistent with a genuine ransomware attack.
Ransomware in the wild
Of the 1,180 respondents, 153 self-reported as having been victims of a ransomware attack.
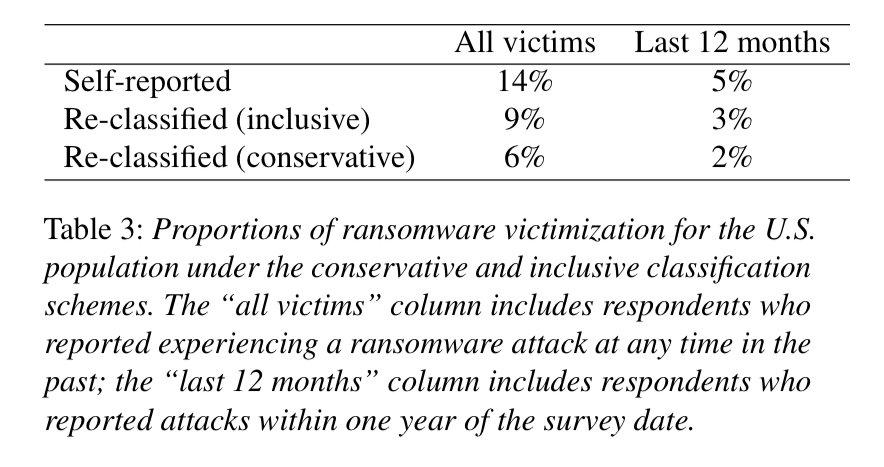
Following reclassification, we estimate that the overall proportion of the U.S. population reporting a ransomware infection at any time in the past ranges between 6%(std error= 1%, n=63) under the conservative regime, and 9% (std error=1%, n=96) under the inclusive regime. We similarly estimate that between 2% and 3% of the U.S. population were affected over the one year period between June 2016 to June 2017 under the conservative and inclusive regimes, respectively.
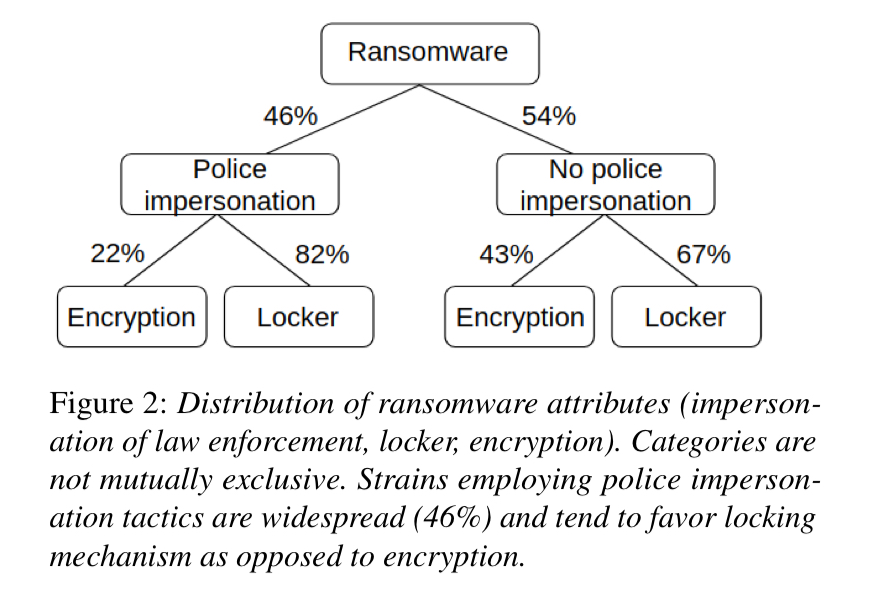
Ransomware that locks the computer (74% of cases) is more common than ransomware employing encryption (35%) (That doesn’t add up to 100%, there’s self-reporting for you!). In 46% of cases the ransomware impersonated a law-enforcement agency, typically with a message such as “Illegal files detected. FBI has locked your computer. Purchase a prepaid VISA and pay fine online…”.
The median ransom demand was $250, the average $530.
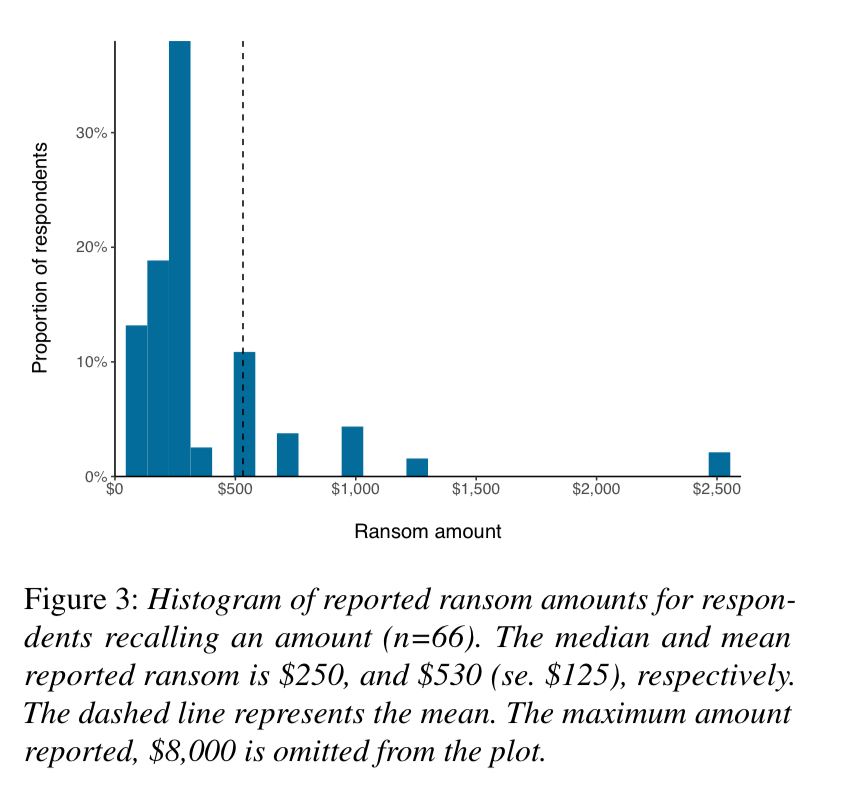
Interestingly, cryptocurrency as a payment method is only requested in a minority of cases: wire transfers and pre-paid cash vouchers seem to be the preferred methods.

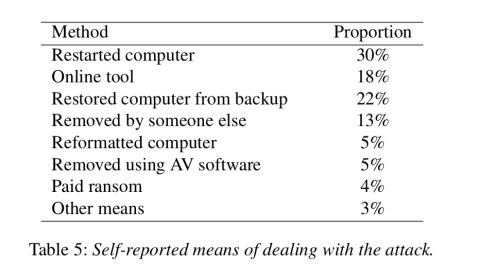
Only 4% of victims (n=6) actually paid the ransom. Access was restored in all of these cases. Tactics used to deal with an attack are summarised in the table below:
Risk prediction factors
Given the potentially high cost of a ransomware infection, a natural follow-up question is whether it is possible to identify the set of at-risk users.
Using features extracted from the survey responses, the authors train two models: a linear (lasso) model and a gradient-boosted-tree model. The outputs from the lasso model (both performed similarly) are re-scaled and rounded to yield integer weights from 1 to 10.
The final risk assessment rubric is based on six factors: use of two-factor authentication, data backup habits, encryption of hard drive, frequency of using torrent services, password protection for login, and previous experience with online scams.
The list of questions and the associated response scores (higher = more likely to be infected) is given in the table below.

The total score for a user maps into an overall probability of ransomware infection within 12 months as shown in the following plot.

The last word
Our survey results shed new light on the scale of ransomware in the general population and the actions users took in response. Our estimated victimization rate of 2-3% of the population per year suggests millions of ransomware cases per year.
With a U.S. population of ~200M, let’s call it 4M infections/year. We know that 4% of respondents paid the ransom, so that’s 160,000 ransom payments. Frustratingly, although we’re told the median ransom demand is $250, I couldn’t see any data on the ransom demanded in the cases where users actually paid, but you’d expect a lower ransom is more likely to be paid. If we say $200 per paid ransom as a guess, that means the ransomware ‘industry’ is making about $32M a year.
“The list of questions and the associated response scores (higher = more likely to be infected) is given in the table below.”
The list of questions appears to be missing.
Fixed now, thank you! (And the missing table 4 as well – clearly having a bad day when I uploaded that post!!)
“Ransomware that locks the computer (74% of cases) is more common than ransomware employing encryption (35%) (That doesn’t add up to 100%, there’s self-reporting for you!).”
I don’t think this has anything to do with self-reporting – more likely the authors rounded down both numbers.
The estimates of the US population puts it at ~325 million not ~200 million.
The population of the US was 327.1 million in 2018, not ~200 million, per the article.
Philipp Leiner, the responses were not mutually exclusive.