Economic factors of vulnerability trade and exploitation Allodi, CCS’17
Today we’re going on a tour inside a prominent Russian cybercrime market, identified in the paper as ‘RuMarket’ (not its real name). The author infiltrated the market using a fake identity, and was subsequently able to collect data on market activities from 2010 to 2017.
RuMarket is a forum-based market that can be reached from the open Internet. Access to the market requires explicit admission by the market administrators, who validate the access request by performing background checks on the requester… As members of the market, we have access to all the (history of) product information, trades and prices available to active participants. This analysis spans seven years of market activity (July 2010 – April 2017).
The study particularly looks at the trade in vulnerabilities. By far the most activity (by an order of magnitude) surrounds vulnerabilities that are marketed in reference to one or more CVEs. Searching and filtering on vulnerabilities traded by CVE resulted in a set of 89 traded exploits over 57 unique vulnerabilities, that were embedded in 38 different packages. The packages can be one of three different types:
- Standalone packages sell stand-alone exploit that are then personalised by the buyer (e.g., to add their own shellcode).
- Malware packages are exploits embedded in malware packaging services.
- EKITS are exploit packages offered under an ‘exploit-as-a-service’ model in which the seller maintains a service which customers rent to deliver their own attacks.
The authors find 26 standalone packages, 6 malware packages, and 6 exploit kits. The exploit kits of course contain an exploit portfolio within them that the kit owners keep up to date. Over time, the number of vendors trading in the market has been steadily growing:
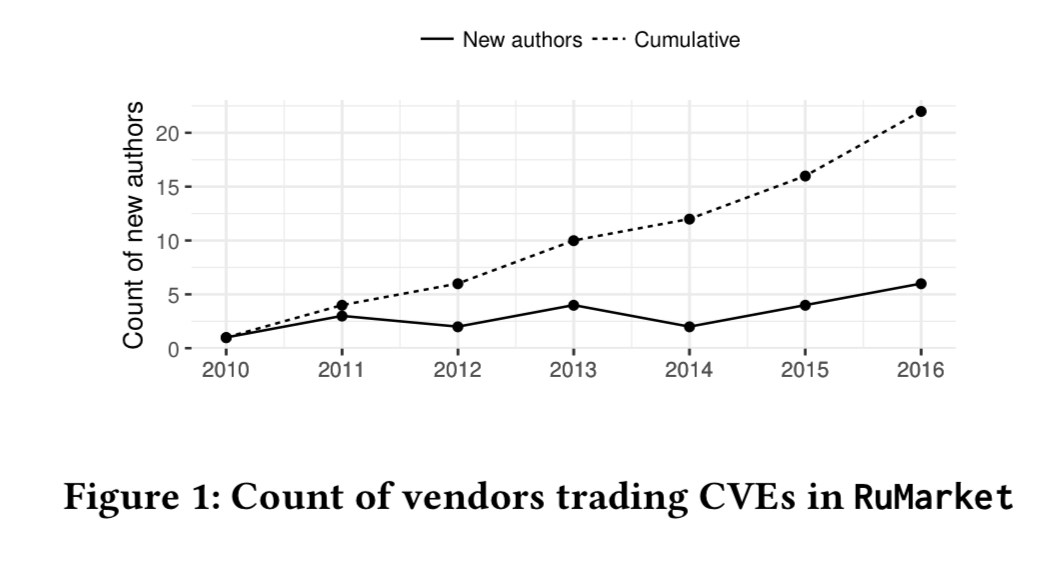
The top EKIT packages remain active in the market board for more than 3 years, whereas standalone and malware packages have a shorter shelf-life. Overall, the average package remains active for a year following initial publication.
The lifecycle of an exploit
Most new exploits appear in the market as standalone products, and later on these get re-packaged into malware and exploit kit distributions. The overall trend is for exploit kits to specialise using fewer, more reliable exploits that at their original introduction.
Standalone exploits therefore seem to play a role in the ‘innovation’ process in RuMarket; this may indicate the presence of an ‘exploit chain’ whereby the most reliable and effective standalone exploits are selected for future inclusion in exploit kit products for deployment at scale.
The top 2.5% of standalone exploits are published in the market within a week of the public disclosure of the corresponding CVE, the top 25% within 40 days, and the top 50% within 2.5 months. The gap between CVE disclosure and exploits packaged in malware or exploit kits is much longer – about half a year on average. Overall, most packaged exploits take around four months from disclosure date to be published.
If we look at the speed of exploit packaging by year though, a trend emerges:
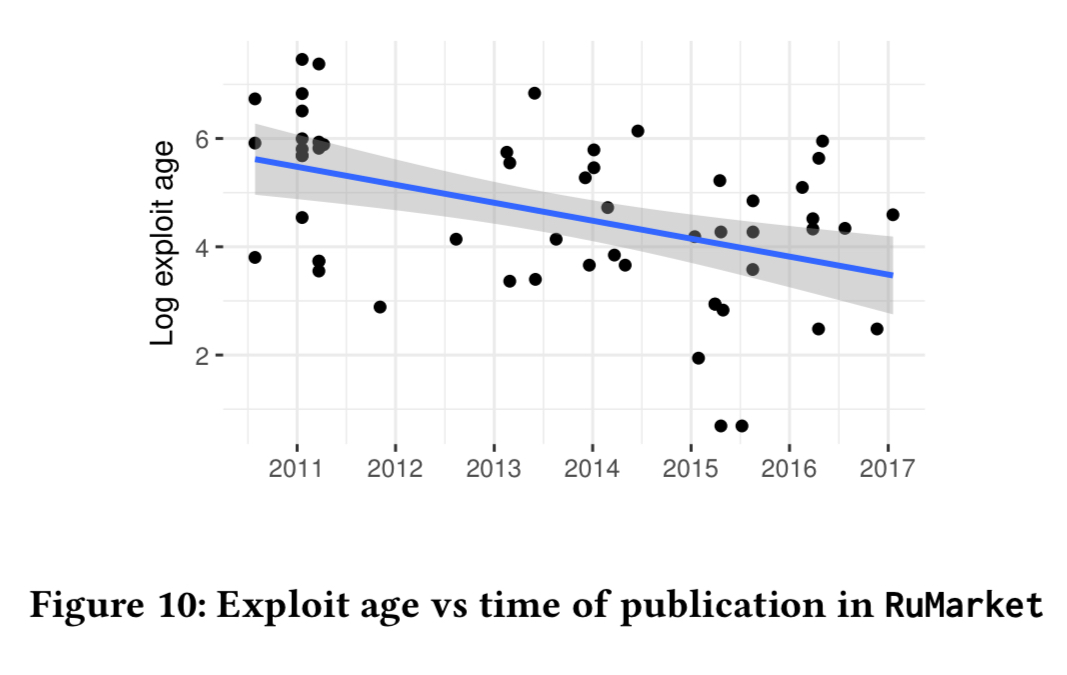
We observe that the mean exploit age decreases steadily for more recent publication dates, indicating that exploit vendors are becoming faster in releasing exploits for newly disclosed vulnerabilities. The coefficient of linear regression indicates that exploits appear at an approximately 30% faster rate every year.
Exploit targets
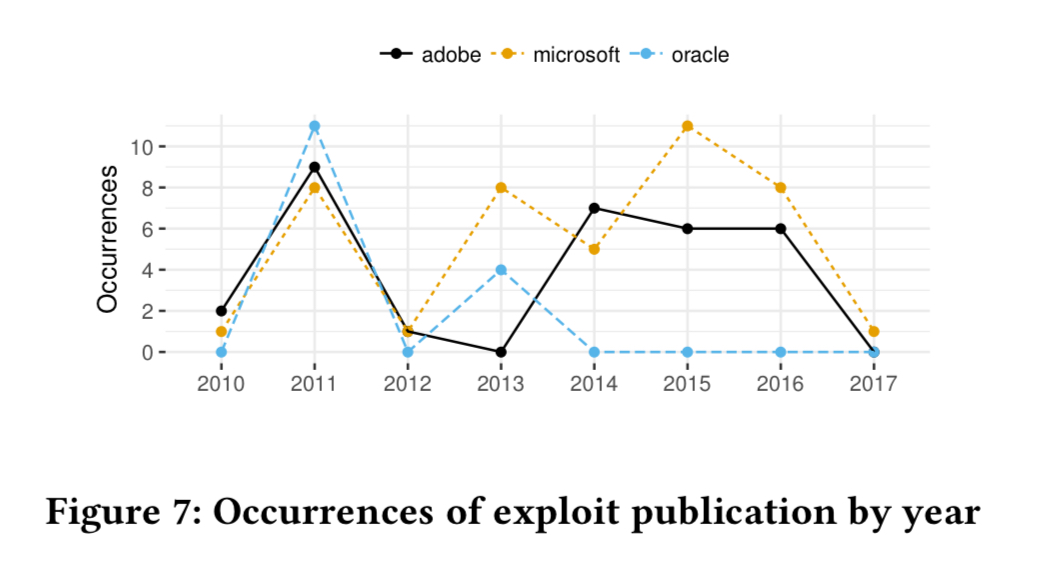
The favourite exploit targets are Microsoft, Adobe, and Oracle products.
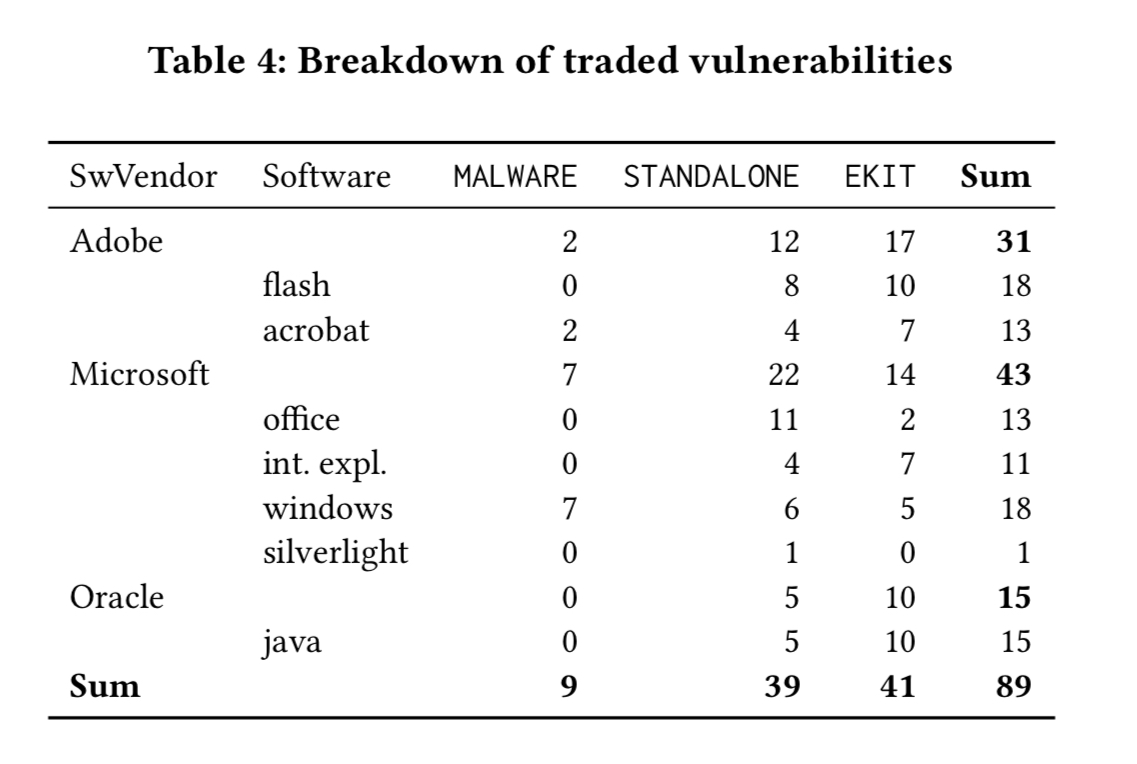
Microsoft vulnerabilities account for more than half of the standalone products. After 2013, with the release of plug-in blocking in browsers and improvements to the default security settings in Java, the packaging of Oracle exploits drops off.
How much is that exploit in the window?
Standalone packages mostly bundle a single exploit, and trade for up to 8000 USD, with a mean price of 2000 USD. Malware packages trade at between 400 and 4000 USD, with most in the 1000-2000 USD range. Exploit kits are typically rented for a period of two to three weeks. Basic exploit kits go for 150-400 USD, and those embedding a wider range of exploits rent for 400-2000 USD. The prices for standalone and malware packages show an increasing trend, whereas exploit kit prices are steadily decreasing.
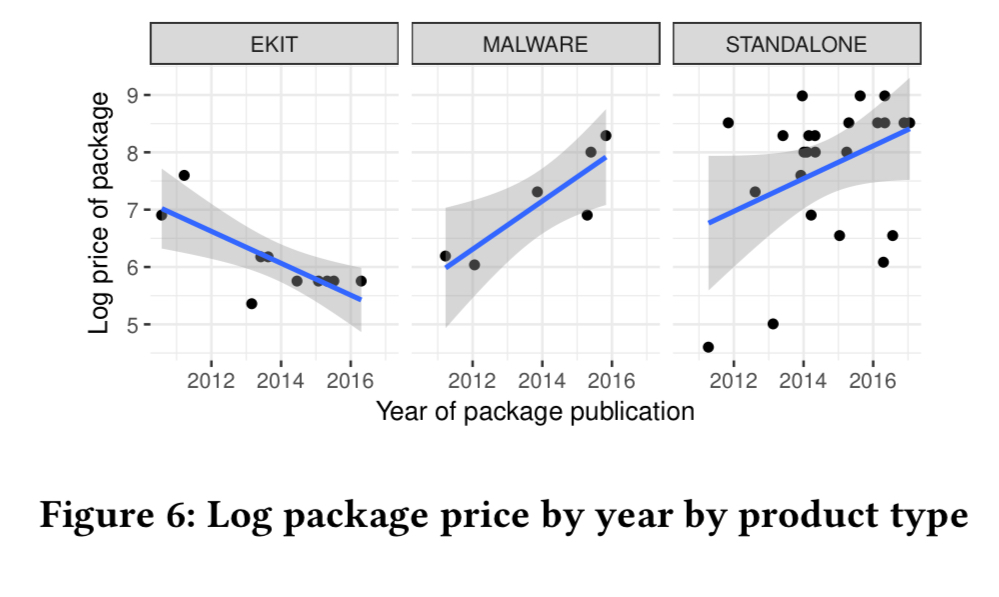
If we break the figures down by exploit target, we see that Microsoft exploits are the most expensive, and within the Microsoft category, exploits targeting Office and Windows are the most expensive of all. (Which makes sense, because these give the attacker the most potential targets).
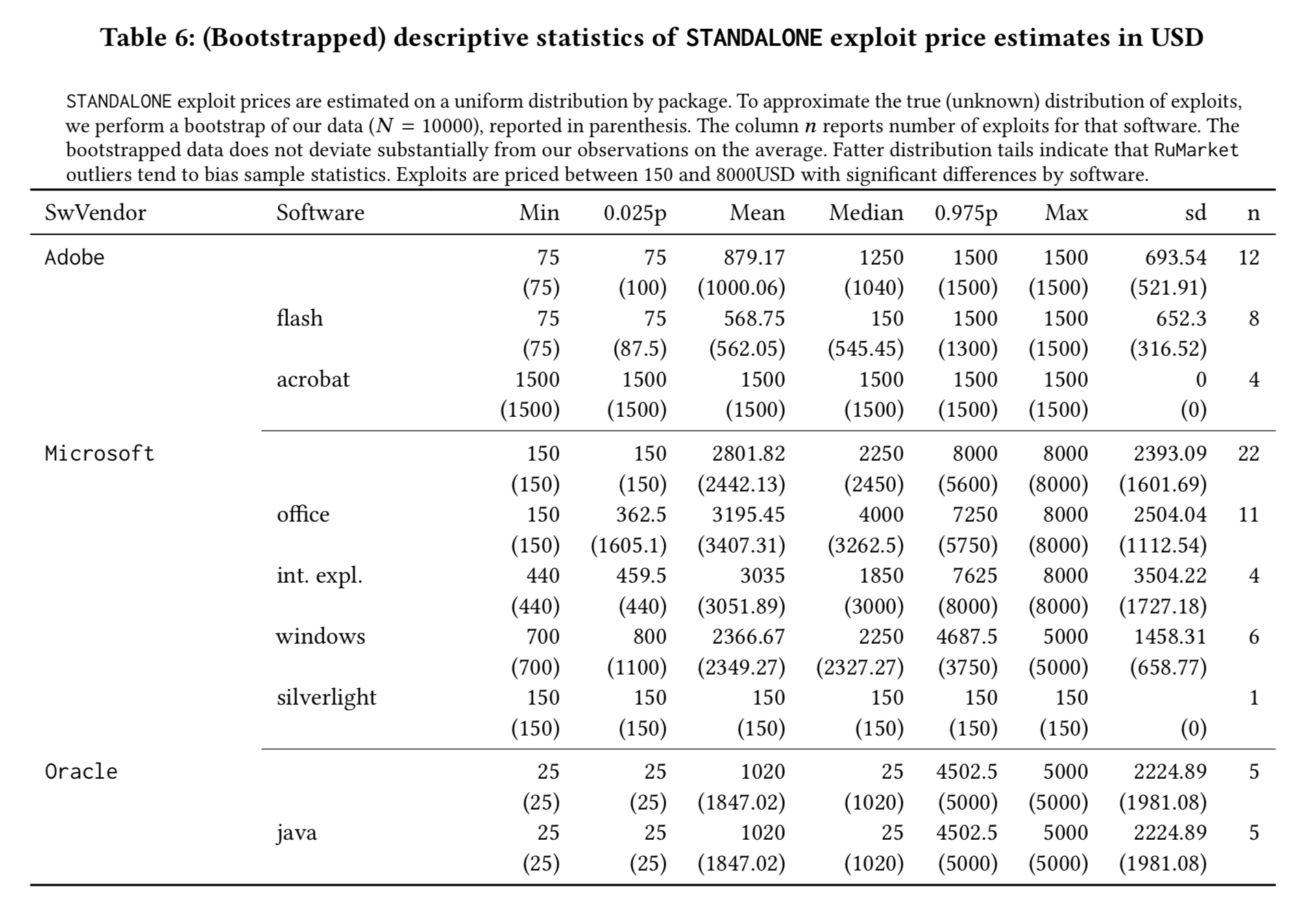
We find that baseline prices for exploits vary widely by software vendor, and are negatively correlated with the age of the exploit; Adobe and Microsoft exploits retain their value significantly longer than Oracle exploits. This may indicate a prolonged economic interest in the exploitation of Microsoft and Adobe vulnerabilities, a finding consistent with related work on the persistence of vulnerabilities on end-user systems.
Are traded exploits used in the wild?
Symantec’s threat explorer and attack signature databases contain information on exploits in the wild, with associated CVE-IDs. Thus it becomes possible to look at trading activity of packaged exploits, and compare it to attacks in the wild.
Exploits with more active forum discussions correlate with a higher chance of exploitation in the wild:
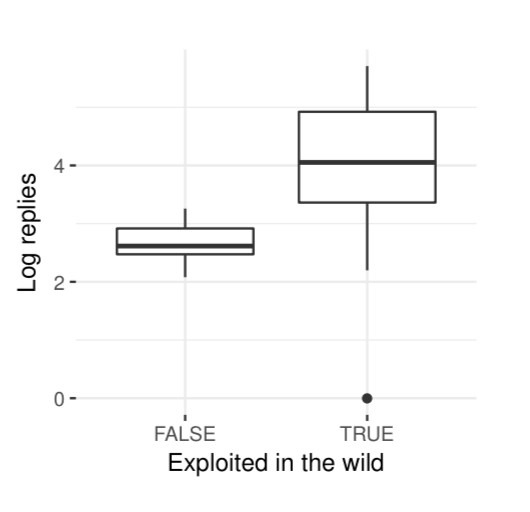
Moreover, the lower the cost of the exploit package, the more likely it is to see the exploit used in the wild:
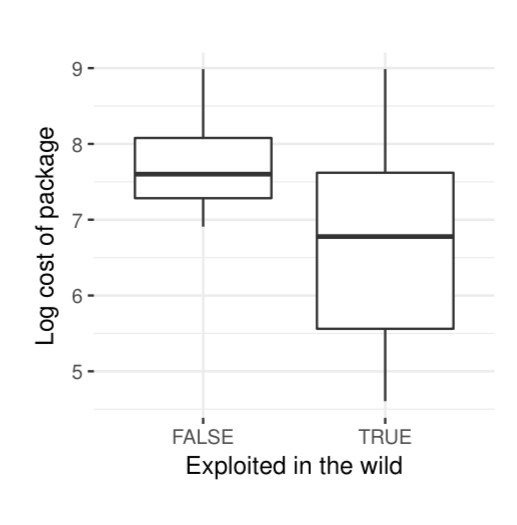
…everything else being equal, exploits bundled in more expensive packages are less likely to be detected in the wild than comparable exploits bundled in less expensive packages. These findings weigh favorably on the existence of a relation between market activity and exploit deployment in the wild.
Exploit kits play an important role here. The exploit kit model allows vendors to reduce their exploit development and deployment costs, thus offering exploits at lower prices. The combination of lower prices and ‘as-a-service’ delivery makes the exploits available to a wider audience, generating more attacks overall.
This suggests that the criminal business model may play a central role in the diffusion of cyber-attacks, and calls for additional studies characterizing this effect.
The severity of the vulnerability also matters. Critical vulnerabilities with exploits traded in RuMarket have a much higher chance of exploitation (93%) than non-critical vulnerabilities (62%).
Bug bounties
The prices available for exploits in modern bug-bounty programs are roughly in line or below the prices for the same exploits on RuMarket. Thus it is still more profitable for a vendor to sell their exploits to different buyers multiple times on the RuMarket than to move to ‘legitimate’ vulnerability markets as in the latter case you can trade the exploit only once. (And what’s stopping a vendor from trading an exploit in both markets, on the assumption that patching in the wild takes time???).
The last word
Our findings quantify a strong correlation between market activities and likelihood of exploit. We find that the analyzed market shows signs of expansion, and that exploit-as-a-service models may allow for drastic cuts in exploit development costs. Further, we find that exploit prices are aligned with or above those of ‘legitimate’ vulnerability markets, supporting work on the identification of incentives for responsible vulnerability disclosure and attack economics.
One thought on “Economic factors of vulnerability trade and exploitation”
Comments are closed.