Understanding malvertising through ad-injecting browser extensions– Xing et al., WWW 2015.
Be careful what browser extensions you install. Some ad networks have started to offer browser extension developers an opportunity to monetise their work, and in this study Xing et al. show that of the 292 Chrome browser extensions in their survey which inject ads, 56 of these participate in malvertising using 16 different ad networks, and a total user base of 602,417.
…compared to ads “naturally” published (without any browser extension intercession) by popular websites, ad-injecting extensions tend to serve a larger fraction of malicious ads. We attribute this to the observation that popular websites partner with large reputable ad networks, whereas extensions utilize smaller ad networks that devote insufficient efforts to identifying and mitigating malicious advertisers. Second, in contrast to previous studies that found only a low fraction of malicious ads, we observed that some ad networks serve only malicious ads. This is presumably because these ad networks and miscreants collude to conduct malvertising, or because miscreants effectively own these ad networks and use them for serving malicious ads. Finally, we found that ad-injecting extensions can make malvertising more detrimental, because some ad networks are unscrupulous on abusing the privileges that ad-injecting extensions offer.
Here’s an example of injected ads in a google search results page, placed there by the “Translate Selection” chrome extension. The user searched for bags – the top highlighted region shows the google sponsored ads, the bottom (red) highlighted the ads injected by extension.
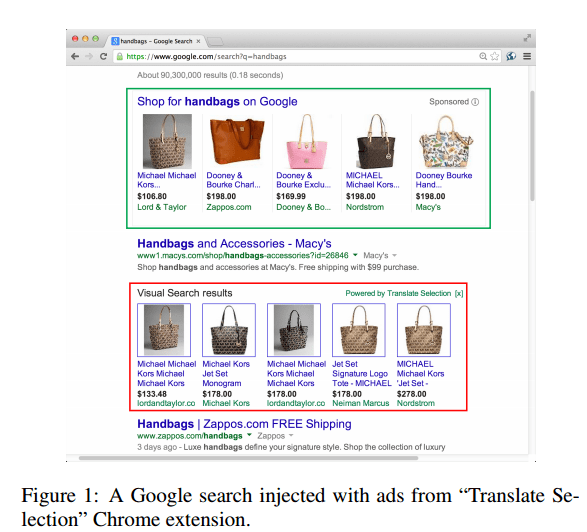
There are three main types of ad injection practices:
- Injecting ads relevant to search terms, as we just saw
- Injecting ads on web pages related to online retailers (e.g. amazon, ebay, etc.). When a product is browsed on these pages, the extension sends the browsing session context to a third-party advertisement service, which retrieves similar or related products, and then shows these ads overlayed on the existing website content.
- Aggressively inserting ads on almost every page the user visits. “This practice can often degrade the user’s experience by showing pop-ups or other forms of annoying ads.”
It is relatively straightforward for extension developers to monetize their extensions through ad injection. Similar to existing ad networks and exchanges, there exists a thriving market of ad networks that provide JavaScript ad injection libraries for extension developers to integrate with their applications.
The authors built a tool called Expector that was used to investigate browser extension malvertisement practice. Expector is built using Node.js and Selenium. It spawns a Chrome instance and loads a Chrome extension for pre-parsing (to identify triggering websites for the second category of ad injection described above). Using the remote debugger interface, they are then able to intercept all JavaScript function invocations. Expector was set to work on all 18,030 extensions listed in the Chrome web store.
Expector reported 303 extensions as adware, which accounts for 1.7% of extensions on the Google Chrome store. We manually installed each of these and inspected their source code, and found that 292 of these are indeed adware… this indicated a very low false positive rate of 3.6%.
The team then studied the ad-injecting extensions that Expector identified…
Understanding malvertisements served by extensions
Every ad-injecting extension identified by Expector is installed in a browser, and then Expector browses the top 1000 Alexa website and activates a click event on all ads that appear during the browsing session. 16 out of the 67 (24%) of ad network domains delivered malicious ads that redirected users to drive-by-download landing pages.
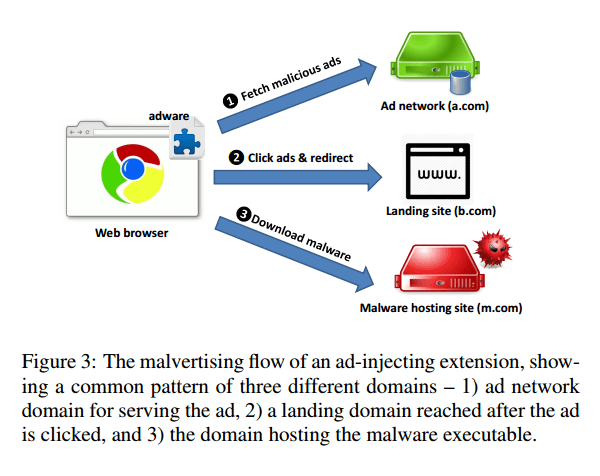
For these 16 ad network domains, we note that malicious executables are typically not hosted on the same site as the landing pages of the malicious ads. A common case we observed is depicted in Figure 3 (below) where the ad-injecting extension fetches ads from an ad network (a.com). When a user clicks the ad, she is redirected to a landing page residing on a different domain – a malicious ad landing domain (b.com). Finally, the malware itself is typically hosted on a third domain (m.com). We assume that this is because separating ad landing domains from malware hosting domains makes it more difficult for browser companies, such as Google (via their Safe browsing API), Firefox and Apple from labeling the malicious landing sites as malware site.
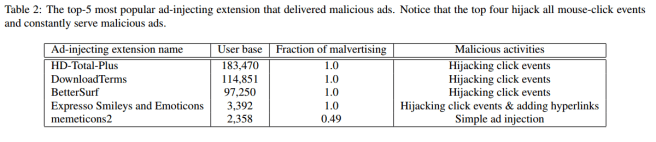
13 out of these 16 ad network domains delivered only malicious advertisements. The top 5 most popular ad-injecting extensions identified are shown in table 2 below.
Further analysis found that the ad networks used for extension based ad-injection only entertain business with advertisers and extension developers, but not with website owners (publishers). Do users actually go on to download malware after visiting malvertising landing pages?
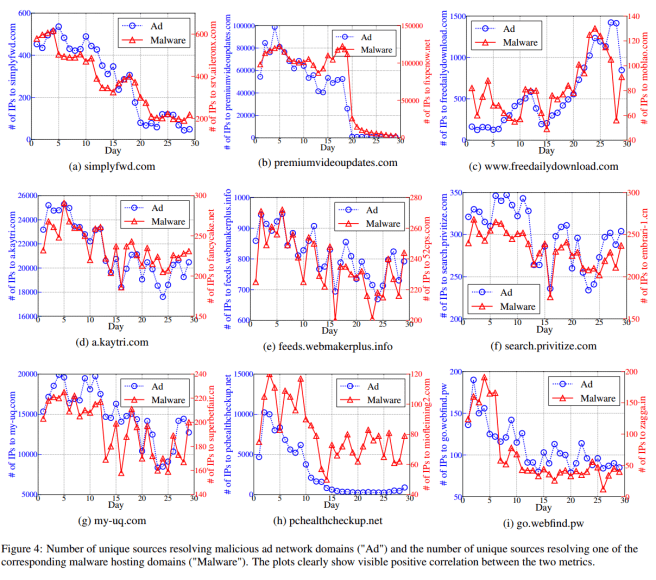
Ideally, we would like to show a causality relationship between downloading malware and receiving ads from the extensions. However, to this end one must obtain complete temporal HTTP flows of many users, which we do not have. Instead, we use our DNS dataset and show strong temporal correlation between the users that resolve the ad network domains and the malware hosting domains.
(Click for larger view).
In some cases, almost 47% of users that resolve an ad network domain also resolve a malware domain. Those extensions exhibiting high overlap ratios use dubious techniques such as abusing extension privilege to hijack all mouse click events.
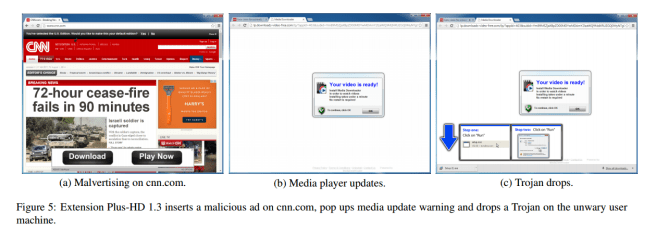
For example, Figure 5 (below) shows the consequences of installing a Chrome extension called Plus-HD 1.3 (now removed from the Chrome extensions store). When the user visits a page, such as http://www.cnn.com, a popup is injected at the bottom of the browser window (not the bottom of the page!). When an unwary user that clicks anywhere on the page (not only on the buttons), a new tab opens up, showing as if a video is ready for watching, but indicates that the user needs to download and install a “Media Downloader”. If the user indeed clicks, the malware is downloaded and the user is prompted to execute it.
In future work, the authors hope to extend Expector to also process extensions of other popular browsers.
One thought on “Understanding malvertising through ad-injecting browser extensions”
Comments are closed.