Click Trajectories: End-to-end analysis of the spam value chain – Levchenko et al. IEEE Symposium on Security and Privacy, 2011
This week we’re going to be looking at some of the less desirable corners of the internet: spam, malvertisements, click-jacking, typosquatting, and friends. To kick things off, today’s paper gives an insight into the end-to-end spam value chain. If we really want to stop spam it turns out, talk to the banks…
As an advertising medium, spam ultimately shares the underlying business model of all advertising. So long as the revenue driven by spam campaigns exceeds their cost, spam remains a profitable enterprise. This glib description belies the complexity of the modern spam business…
How does spam work?
There’s much more to spam than just the email! There are three key stages – advertising, click support, and realization – supported by a whole value chain.
Advertising concerns how potential customers are reached. This paper focuses on email spam, but the same business model applies to blog spam, twitter spam, blackhat SEO, and sponsored advertising. Efforts to shut down SMTP proxies and the introduction of IP blacklisting led to an arms escalation and the use of more sophisticated delivery vehicles….
These include botnets, webmail spam, and IP prefix hijacking. Moreover, the market for spam services has stratified over time; for example, today it is common for botnet operators to rent their services to spammers on a contract basis.
Once the advert has been delivered, spammers usually depend on the target to click on an embedded link. A great many moving parts are involved in this click support. Due to URL and domain blacklisting, site takedowns by ISPs, and domain takedowns by registrars, spammers employ redirection strategies.
Many spammers advertise URLs that, when visited, redirect to additional URLs. Redirection strategies primarily fall into two categories: those for which a legitimate third party inadvertently controls the DNS name resource for the redirection site (e.g. free hosting, URL shorteners, or compromised web sites), and those which the spammers themselves, or perhaps parties working on their behalf, manage the DNS name resources (e.g. a “throwaway” domain such as minesweet.ru redirecting to a more persistent domain such as greatjoywatches.com).
Spammers typically purchase domains from domain resellers, who purchase domains in bulk via multiple sources and sell them to the underground trade. Alternative they may buy them “directly from a spam ‘affiliate program’ that makes domains available to their affiliates as part of their ‘startup package.'” Registered domains must have supporting name server infrastructure…
Since such resources are vulnerable to takedown requests, a thriving market has arisen in so-called “bulletproof” hosting services that resist such requests in exchange for a payment premium.
The web servers that the name servers point to can also take advantage of bulletproof hosting to resist takedown pressure. (If you want to know how to build resilient systems it turns out, talk to the spammers!) Many spammers further obfuscate the hosting relationship using fast-flux DNS in which domain records have short-lived associations with IP addresses, “and the mapping infrastructure can spread the domain’s presence over a large number of machines (frequently many thousands of compromised hosts that in turn proxy requests back to the actual content server.”
Today, spammers operate primarily as advertisers, rarely handling the back end of the value chain. Such spammers often work as affiliates of an online store, earning a commission (typically 30–50%) onthe sales they bring in. The affiliate program typically provides the storefront templates, shopping cart management, analytics support, and even advertising materials. In addition, the program provides a centralized Web service interface for affiliates to track visitor conversions and to register for payouts (via online financial instruments such as WebMoney). Finally, affiliate programs take responsibility for contracting for payment and fulfilment services with outside parties. Affiliate programs have proven difficult to combat directly—although, when armed with sufficient legal jurisdiction, law enforcement has successfully shut down some programs.
Realization is the final stage in the process – once the customer has been convinced to purchase a product the customer’s payment must be processed and the product request fulfilled. Stores support standard credit card payments to extract value from the broadest possible customer base.
A credit card transaction involves several parties in addition to the customer and merchant; mony is transferred from the issuing bank (the customer’s bank) to the acquiring bank (the bank of the merchant) via a card association network (i.e. Visa or MasterCard). In addition to the acquiring bark, issuing bank, and card association, the merchant frequently employs the services of a payment processor to facilitate this process and act as the technical interface between the merchant and the payment system.
Generally, suppliers offer a direct shipping service (drop shipping), so affiliate programs can structure themselves around just-in-time fulfilment and over any risk and overhead from warehousing and shipping the product themselves.
A study of the spam ecosystem
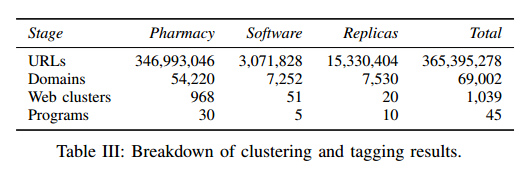
The authors crawled and studied nearly 1 billion spam URLs, and clustered the results by type, homing in on pharmacy, software, and replicas as the three major areas. Table III below shows the number of URLs in each category, and the number of domains, web clusters, and affiliate programs that sit behind them.
For a subset of these sites, the authors also purchased goods being offered for sale.
All of our purchases were conducted using prepaid Visa payment cards contracted through a specialty issuer… We had goods shipped to a combination of individual residences and a suite address provided by a local commercial mailbox provider.
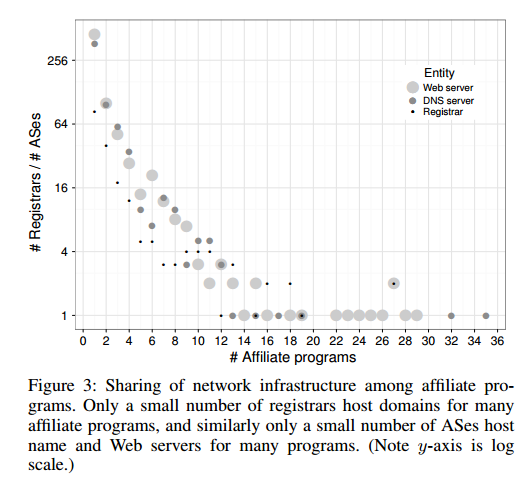
To find possible bottlenecks or weaknesses in the spam value chain, the team looked at the extent to which affiliate programs share infrastructure.
Network infrastructure sharing, when it occurs, is concentrated in a small number of registrars and Autonomous Systems (ASes). Most of these host infrastructure for just one or two affiliate programs.
It turns out that affiliate programs do not in general distributed their infrastructure across large sets of registrars or ASes. Switching costs are very low if a problem is encountered though.
The sharing of payment infrastructure however is substantial.
… of the 76 purchases for which we received transaction information, there were only 13 distinct banks acting as Visa acquirers. Moreover, there is a significant concentration even among this small set of banks. In particular, most herbal and replica purchases cleared through the same bank in St. Kitts (a by-product of ZedCash’s dominance of this market), while most pharmaceutical affiliate programs used two banks (in Azerbaijan and Latvia) and software was handled entirely by two banks (in Latvia and Russia).
Despite the claims of some programs that spammers have stolen their templates and that they do not allow spam-based advertising, analysis of the payment process (bank, order number format, email template etc.) suggests otherwise.
Fulfilment for physical goods was sourced from 13 different suppliers, of which eight were seen more than once. All pharmaceutical tablets shipped from India, except for one shipped within the United States (from a minor program), while replicas shipped universally from China. While we received herbal supplement products from China and New Zealand, most (by volume) shipped from within the United States. This result is consistent with our expectation since, unlike the other goods, herbal products have weaker regulatory oversight and are less likely to counterfeit existing brands and trademarks.
Our best hope for combating spam?
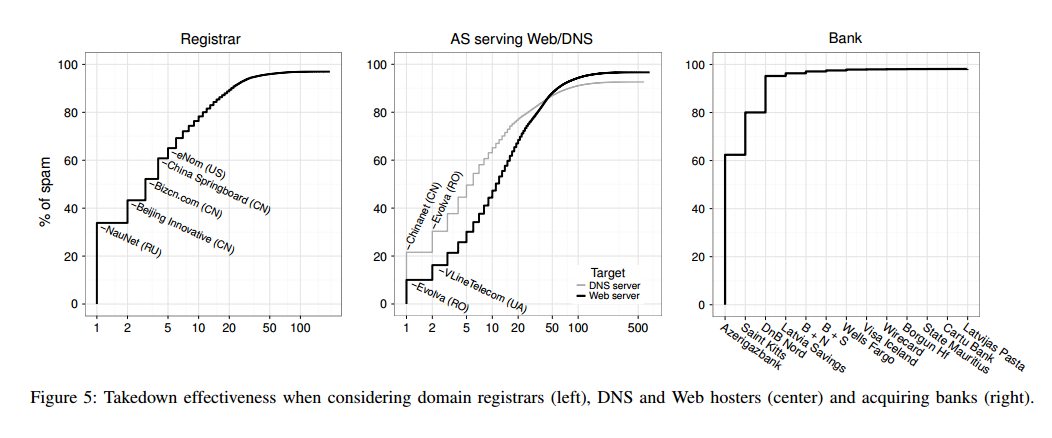
Anti-spam interventions should be evaluated based on their overhead to implement, and their business impact on the spam value chain. Figure 5 shows the effectiveness of takedowns at three different points in the value chain: registrars, web hosters, and acquiring banks:
Takedowns appear to be an effective strategy for registrars and web hosters, but another key issue is the availability of alternatives and their switching cost. Switching costs are low, and new hosts can be provisioned on demand and for low cost.
… it is the banking component of the spam value chain that is both the least studied and, we believe, the most critical. Without an effective mechanism to transfer consumer payments, it would be difficult to finance the rest of the spam ecosystem. Moreover, there are only two networks—Visa and Mastercard—that have the consumer footprint in Western countries to reach spam’s principal customers. While there are thousands of banks, the number who are willing to knowingly process what the industry calls “high-risk” transactions is far smaller. This situation is dramatically reflected in Figure 5 (above) , which shows that just three banks provide the payment servicing for over 95% of the spam-advertised goods in our study.
“More importantly, the replacement cost for new banks is high, both in setup fees and more importantly, in time and overhead.”
Directly engaging with the merchant banks and pressuring them to stop doing business with such merchants is likely to be very slow – likely slower than the time to acquire new banking facilities.
Moreover, due to incongruities in intellectual property protection, it is not even clear that the sale of such goods is illegal in the countries in which such banks are located. Indeed, a sentiment often expressed in the spammer community, which resonates in many such countries, is that the goods they advertise address a real need in the West, and efforts to criminalize their actions are motivated primarily by Western market protectionism.
An alternative strategy woud be for western issuing banks to refuse to settle certain transactions with the banks identified as supporting spam-advertised goods.
It appears plausible that such a “financial blacklist” could be updated very quickly (driven by modest numbers of undercover buys, as in our study) and far more rapidly than the turn-around time to acquire new banking resources – a rare asymmetry favoring the anti-spam community. Furthermore, for a subset of spam-advertised goods there is a legal basis for enforcing such a policy. While we suspect that the political challenges for such an intervention would be significant – and indeed merit thoughtful consideration – we note that a quite similar action has already occurred in restricting U.S. issuers from settling certain kinds of online gambling transactions.